Introduction to hacking , its benefits and scope in future to become Ethical hacker 2022

In this Article I am going to tell you about the Introduction to hacking , its benefits and scope in future to become Ethical hacker so that you will come to know about the basic information about Ethical hacking. As you know that we are offering you the Ethical hacking course so that you can be successful in this field if you wants to have this as a profession in the future. As many of you thought that hacking is illegal and that it has no scope in future and is not good for everyone. Let me clear that hacking is something which is done to hack someone's personal information or sensitive information but its not necessary that we have to become black hat hacker in future. We have to choose Ethical hacking for the future protection of our sensitive information and also the cybersecurity companies are so desperate that they wanted the best Ethical hacker to work with them to protect their sensitive information.
So, if anyone of you are interested to join our course then you can join it and for more information you can contact us.
Now, I am going to tell you about the Introduction to hacking , its benefits and scope in future to become Ethical hacker.
Ethical hacking:
Ethical hacking includes authorized attempts to gain unauthorized access to computer systems, applications, or data. Ethical hacking requires replicating the strategies and behaviors of malicious attackers. This practice helps identify security vulnerabilities so that they can be fixed before malicious attackers can exploit them.
Unlike malicious hackers, ethical hackers have permission and approval from the organizations they hack. Learn how to build a career in testing network security, fighting cybercrime, and improving information security.
Ethical hacking is conducting a security assessment using the same techniques hackers use, but with proper approval and authorization from the organization being hacked. The goal is to leverage cybercriminal tactics, techniques, and strategies to identify potential vulnerabilities and better protect organizations against data and security breaches.
Ethical hackers, also known as white hat hackers, are information security professionals who gain permission to enter computer systems, networks, applications, or other computing resources on behalf of their owners. Companies are asking ethical hackers to uncover potential security flaws that malicious hackers can exploit. The purpose of ethical hacking is to assess the security of a targeted system, network, or system infrastructure and identify vulnerabilities. This process involves finding and exploiting vulnerabilities to determine if unauthorized access or other malicious activity is possible.
What are the meanings and key concepts of ethical hacking?
Ethical hacking is very important as it helps protect your network from cyberattacks. Ethical hacking is a special type of penetration testing performed for security purposes.
Ethical hacking has three main meanings:
- It helps you find vulnerabilities in your network so you can quickly fix them before they can be exploited by criminals and hackers.
- It helps improve security by identifying network vulnerabilities and implementing strong security measures.
- It also helps educate employees about cybersecurity issues so they don't fall for phishing scams and other attacks.
However, to become an ethical hacker, you must first understand her three key concepts of ethical hacking. The three main concepts of ethical hacking are:
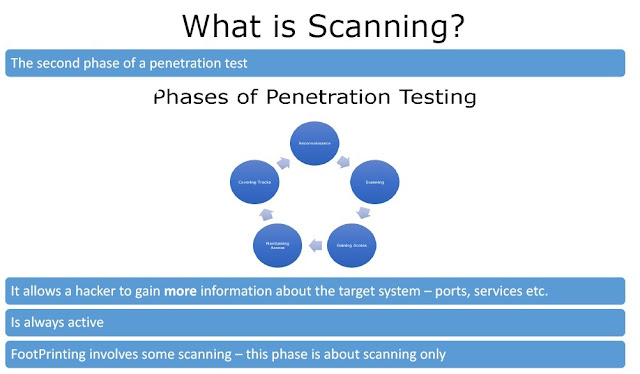
1. Scanning:
A scan identifies the target network, its devices, and their current configuration. This information can be used to identify vulnerabilities and determine which types of ethical hacking attacks are most effective on those devices.
2.Enumeration
Enumeration gathers information about the target network. Usernames and passwords that can be used later in the attack.
3. Exploitation
An exploit is the exploitation of a device vulnerability to gain access to sensitive data or control of that device.
What are the different types of ethical hacking?
Ethical hacking is a complex process involving a combination of skills, techniques, and methods for testing the security of an organization's computer systems. There are many different types of hacking in cybersecurity practice.
1. Black box testing:
black box testing, hackers have no prior knowledge of the system and test software from outside the system before breaking into the system with a brute force approach. For example, when testing a website, you may not know what kind of server the website is running on or what programming language was used to build the website. This type of hack is often considered one of the most dangerous types of hack in cybersecurity and is used to identify network or system vulnerabilities that attackers can exploit. They illegally access personal information such as credit card numbers and bank accounts to sell or use for illegal purposes such as identity theft and fraud. For example, you can use black box testing to check user logins, view account information, change passwords, and log out. Testers don't need to know how to achieve this in the application's code in order to design such tests.
2. white box testing
white box testing, hackers know everything about a system, how it works, and its vulnerabilities before attempting to break into it. White-box testing is often performed by developers who want to see how well a system will hold up under pressure before releasing it into production where attackers will attempt to crack it. They work closely with his IT department and are able to know what's going on under the hood without violating the law, according to company policy. Also, make sure no one hacks into your employer's system. Common examples of white box testing include design reviews, code inspections, data flow analysis, and statement coverage.
3. Gray box testing:
This is a combination of white box and black box testing. Testers have some knowledge of the system, but not all of it, and must use their deductive reasoning skills and technical knowledge to find vulnerabilities in the system or network under test. Gray Hats sometimes use their abilities for good and evil. B. Stealing money via computer viruses created by banks or other companies (meaning they could be viewed as malicious). Examples of grey-box testing include areas such as:
- usability test
- performance test
- security test
This approach helps you understand how well your application performs in a real-world environment. This is important for successful development.
4. Hacking web applications
Web application hacking exploits security holes and vulnerabilities in web-based applications. Web applications are typically written in languages such as HTML, CSS, and JavaScript, but can also be written in other languages such as PHP or Ruby on Rails. Because of the nature of these languages and the way web browsers interpret them, it is possible to perform certain actions on websites without actually being authorized to do so. An example of this is cross-site scripting (XSS), which injects malicious code into the HTML of a website. A well-executed XSS attack can hijack browser and server sessions without access to usernames or passwords. 5. Hacking wireless networks Wireless network hacking is a type of hacking that usually exploits security vulnerabilities in your system to gain unauthorized access to your computer network. A classic example of this is the practice of word-driving, where an attacker drives around with a laptop or other device capable of receiving wireless signals, looking for unprotected or poorly protected networks.
How do I choose an ethical hacking course and certification?
Ethical hacking courses and certifications are the best way to learn to hack. However, choosing the right course can be a daunting task. To make it easier, here are some factors to consider when choosing a course.
1. Period
One of the most important things to look for in any kind of ethical hacking course is the length of the course. Most courses last about nine months, but some courses take up to two years.
2. Cost
The longer the course, the more detailed the concepts are, and the more expensive. Choose a course that fits your schedule and budget.
3. availability
Another thing to note about ethical hacking courses is whether they are available online or offline. Some courses are only available online, while others are only available in physical locations.
Before joining a course, decide which type of learning style you prefer.
4. Authentication
A third thing to consider when choosing an ethical hacking course is whether it comes with a cybersecurity course certificate. If you want to be certified as an ethical hacker, make sure the course you choose offers certification as part of their curriculum.
Career Benefits of Ethical Hacking
New malware, spyware, ransomware, Trojan horses, and worms are growing every day. As a result, hiring ethical hackers has become paramount in securing corporate and government networks and systems. This contributes to the ongoing shortage of cybersecurity professionals to fill vacancies. Security Magazine predicts that 3.5 million cybersecurity jobs will be gone by 2022. According to the US Department of Labor (table below), the average annual salary for an information security analyst (ethical hacker) is about $100,000, while the average salary for a computer programmer is about $84,000. Job prospects for information or cybersecurity analytics are promising, growing at a rapid rate of 28% compared to an average of 7%. Compensation for senior cybersecurity positions such as B. As Chief Information Security Officer, can reach $400,000 per year. It's easy to see why ethical hacking professionals are in such high demand. One Cisco reports that 29% of businesses have lost revenue due to security breaches. According to Forrester Research, 95% of the records broken in 2016 came from his three sectors:
Government, Retail, Technology. Indeed has a list of over 800 active ethical hackers with salaries ranging from $70,000 to $120,000. Our Certified Ethical Hacker course trains you in the advanced practices hackers use to better protect your networks and systems from data breaches and threats. This certified ethical hacking course helps you build your network security skills by mastering advanced techniques in network packet analysis, reverse engineering, and system penetration testing. You can gain a deeper understanding of how hackers think and think, and avoid attacks, or at least minimize the damage to your organization's and authorities' data.
We excels at learning with an accredited ethical hacking course that includes 40 hours of instructor-led learning sessions, an EC Council learning materials kit, and her six months of free access to her CEH v10 lab to practice the tech have a pedigree. You also get lifetime access to high-quality, self-paced eLearning content and live lesson recordings.
Start your career as an ethical hacker today
The ethical hacking profession is rapidly gaining momentum as companies increase their spending to combat cybersecurity threats. If you're passionate about cybersecurity, our certified ethics course is for you. The theory and practical knowledge gained from Our Certified Ethical Hacker curriculum, along with the right knowledge and mindset, can put her on the right path to becoming an Information Security Analyst or Cybersecurity Professional. what are you looking for Get ready for the future by enrolling in Our Certified Ethical Hacking Course.
The future of ethical hacking in Pakistan:
The field of ethical hacking has a very bright future in Pakistan. The need for ethical hackers is expected to continue to grow in the coming years. India is a country with a large number of people working in the information technology field. The growing need for responsible computer he hackers in India is due to various factors.
The main reason for this is the increase in cyberattacks. As more people use the Internet, the frequency of cyberattacks is also increasing. Various organizations and companies have been targeted by this type of attack. Malicious attackers are always looking for new entry points to exploit system flaws. They use various hacking techniques to gain access to networks and steal sensitive information. Ethical hackers help companies find vulnerabilities in computer systems so that bugs can be fixed before adversaries can exploit them. The second factor is the growing awareness of the importance of maintaining strong cybersecurity measures. At this point, both people and businesses recognize the importance of maintaining good cybersecurity.
They recognize that cyberattacks can expose personal data and affect an organization's day-to-day operations. Ethical hackers help companies protect their networks from various types of cyberattacks. The strict nature of rules and regulations is her third factor. Governments issue many rules and regulations to ensure that businesses comply with cybersecurity standards. Businesses can comply with rules and regulations with the help of ethical hackers. Fourth on the list of reasons is the need to protect a company's reputation. Attacks from cyberspace can damage an organization's reputation. Ethical hackers help protect a company's image by finding and fixing vulnerabilities found in an organization's systems. The sixth reason is because we want to keep costs down. Organizations can suffer financial losses as a direct result of cyberattacks. Ethical hackers help companies reduce operating costs by finding and fixing vulnerabilities in company systems.
Ethical hackers are an invaluable asset to a company's efforts to maintain privacy and security. It helps companies identify vulnerabilities in their systems and implement fixes for those vulnerabilities.







No comments:
Post a Comment