Thursday, January 19, 2023
Monday, November 21, 2022
Introduction to hacking , its benefits and scope in future to become Ethical hacker 2022
In this Article I am going to tell you about the Introduction to hacking , its benefits and scope in future to become Ethical hacker so that you will come to know about the basic information about Ethical hacking. As you know that we are offering you the Ethical hacking course so that you can be successful in this field if you wants to have this as a profession in the future. As many of you thought that hacking is illegal and that it has no scope in future and is not good for everyone. Let me clear that hacking is something which is done to hack someone's personal information or sensitive information but its not necessary that we have to become black hat hacker in future. We have to choose Ethical hacking for the future protection of our sensitive information and also the cybersecurity companies are so desperate that they wanted the best Ethical hacker to work with them to protect their sensitive information.
So, if anyone of you are interested to join our course then you can join it and for more information you can contact us.
Now, I am going to tell you about the Introduction to hacking , its benefits and scope in future to become Ethical hacker.
Ethical hacking:
Ethical hacking includes authorized attempts to gain unauthorized access to computer systems, applications, or data. Ethical hacking requires replicating the strategies and behaviors of malicious attackers. This practice helps identify security vulnerabilities so that they can be fixed before malicious attackers can exploit them.
Unlike malicious hackers, ethical hackers have permission and approval from the organizations they hack. Learn how to build a career in testing network security, fighting cybercrime, and improving information security.
Ethical hacking is conducting a security assessment using the same techniques hackers use, but with proper approval and authorization from the organization being hacked. The goal is to leverage cybercriminal tactics, techniques, and strategies to identify potential vulnerabilities and better protect organizations against data and security breaches.
Ethical hackers, also known as white hat hackers, are information security professionals who gain permission to enter computer systems, networks, applications, or other computing resources on behalf of their owners. Companies are asking ethical hackers to uncover potential security flaws that malicious hackers can exploit. The purpose of ethical hacking is to assess the security of a targeted system, network, or system infrastructure and identify vulnerabilities. This process involves finding and exploiting vulnerabilities to determine if unauthorized access or other malicious activity is possible.
What are the meanings and key concepts of ethical hacking?
Ethical hacking is very important as it helps protect your network from cyberattacks. Ethical hacking is a special type of penetration testing performed for security purposes.
Ethical hacking has three main meanings:
- It helps you find vulnerabilities in your network so you can quickly fix them before they can be exploited by criminals and hackers.
- It helps improve security by identifying network vulnerabilities and implementing strong security measures.
- It also helps educate employees about cybersecurity issues so they don't fall for phishing scams and other attacks.
However, to become an ethical hacker, you must first understand her three key concepts of ethical hacking. The three main concepts of ethical hacking are:
1. Scanning:
A scan identifies the target network, its devices, and their current configuration. This information can be used to identify vulnerabilities and determine which types of ethical hacking attacks are most effective on those devices.
2.Enumeration
Enumeration gathers information about the target network. Usernames and passwords that can be used later in the attack.
3. Exploitation
An exploit is the exploitation of a device vulnerability to gain access to sensitive data or control of that device.
What are the different types of ethical hacking?
Ethical hacking is a complex process involving a combination of skills, techniques, and methods for testing the security of an organization's computer systems. There are many different types of hacking in cybersecurity practice.
1. Black box testing:
black box testing, hackers have no prior knowledge of the system and test software from outside the system before breaking into the system with a brute force approach. For example, when testing a website, you may not know what kind of server the website is running on or what programming language was used to build the website. This type of hack is often considered one of the most dangerous types of hack in cybersecurity and is used to identify network or system vulnerabilities that attackers can exploit. They illegally access personal information such as credit card numbers and bank accounts to sell or use for illegal purposes such as identity theft and fraud. For example, you can use black box testing to check user logins, view account information, change passwords, and log out. Testers don't need to know how to achieve this in the application's code in order to design such tests.
2. white box testing
white box testing, hackers know everything about a system, how it works, and its vulnerabilities before attempting to break into it. White-box testing is often performed by developers who want to see how well a system will hold up under pressure before releasing it into production where attackers will attempt to crack it. They work closely with his IT department and are able to know what's going on under the hood without violating the law, according to company policy. Also, make sure no one hacks into your employer's system. Common examples of white box testing include design reviews, code inspections, data flow analysis, and statement coverage.
3. Gray box testing:
This is a combination of white box and black box testing. Testers have some knowledge of the system, but not all of it, and must use their deductive reasoning skills and technical knowledge to find vulnerabilities in the system or network under test. Gray Hats sometimes use their abilities for good and evil. B. Stealing money via computer viruses created by banks or other companies (meaning they could be viewed as malicious). Examples of grey-box testing include areas such as:
- usability test
- performance test
- security test
This approach helps you understand how well your application performs in a real-world environment. This is important for successful development.
4. Hacking web applications
Web application hacking exploits security holes and vulnerabilities in web-based applications. Web applications are typically written in languages such as HTML, CSS, and JavaScript, but can also be written in other languages such as PHP or Ruby on Rails. Because of the nature of these languages and the way web browsers interpret them, it is possible to perform certain actions on websites without actually being authorized to do so. An example of this is cross-site scripting (XSS), which injects malicious code into the HTML of a website. A well-executed XSS attack can hijack browser and server sessions without access to usernames or passwords. 5. Hacking wireless networks Wireless network hacking is a type of hacking that usually exploits security vulnerabilities in your system to gain unauthorized access to your computer network. A classic example of this is the practice of word-driving, where an attacker drives around with a laptop or other device capable of receiving wireless signals, looking for unprotected or poorly protected networks.
How do I choose an ethical hacking course and certification?
Ethical hacking courses and certifications are the best way to learn to hack. However, choosing the right course can be a daunting task. To make it easier, here are some factors to consider when choosing a course.
1. Period
One of the most important things to look for in any kind of ethical hacking course is the length of the course. Most courses last about nine months, but some courses take up to two years.
2. Cost
The longer the course, the more detailed the concepts are, and the more expensive. Choose a course that fits your schedule and budget.
3. availability
Another thing to note about ethical hacking courses is whether they are available online or offline. Some courses are only available online, while others are only available in physical locations.
Before joining a course, decide which type of learning style you prefer.
4. Authentication
A third thing to consider when choosing an ethical hacking course is whether it comes with a cybersecurity course certificate. If you want to be certified as an ethical hacker, make sure the course you choose offers certification as part of their curriculum.
Career Benefits of Ethical Hacking
New malware, spyware, ransomware, Trojan horses, and worms are growing every day. As a result, hiring ethical hackers has become paramount in securing corporate and government networks and systems. This contributes to the ongoing shortage of cybersecurity professionals to fill vacancies. Security Magazine predicts that 3.5 million cybersecurity jobs will be gone by 2022. According to the US Department of Labor (table below), the average annual salary for an information security analyst (ethical hacker) is about $100,000, while the average salary for a computer programmer is about $84,000. Job prospects for information or cybersecurity analytics are promising, growing at a rapid rate of 28% compared to an average of 7%. Compensation for senior cybersecurity positions such as B. As Chief Information Security Officer, can reach $400,000 per year. It's easy to see why ethical hacking professionals are in such high demand. One Cisco reports that 29% of businesses have lost revenue due to security breaches. According to Forrester Research, 95% of the records broken in 2016 came from his three sectors:
Government, Retail, Technology. Indeed has a list of over 800 active ethical hackers with salaries ranging from $70,000 to $120,000. Our Certified Ethical Hacker course trains you in the advanced practices hackers use to better protect your networks and systems from data breaches and threats. This certified ethical hacking course helps you build your network security skills by mastering advanced techniques in network packet analysis, reverse engineering, and system penetration testing. You can gain a deeper understanding of how hackers think and think, and avoid attacks, or at least minimize the damage to your organization's and authorities' data.
We excels at learning with an accredited ethical hacking course that includes 40 hours of instructor-led learning sessions, an EC Council learning materials kit, and her six months of free access to her CEH v10 lab to practice the tech have a pedigree. You also get lifetime access to high-quality, self-paced eLearning content and live lesson recordings.
Start your career as an ethical hacker today
The ethical hacking profession is rapidly gaining momentum as companies increase their spending to combat cybersecurity threats. If you're passionate about cybersecurity, our certified ethics course is for you. The theory and practical knowledge gained from Our Certified Ethical Hacker curriculum, along with the right knowledge and mindset, can put her on the right path to becoming an Information Security Analyst or Cybersecurity Professional. what are you looking for Get ready for the future by enrolling in Our Certified Ethical Hacking Course.
The future of ethical hacking in Pakistan:
The field of ethical hacking has a very bright future in Pakistan. The need for ethical hackers is expected to continue to grow in the coming years. India is a country with a large number of people working in the information technology field. The growing need for responsible computer he hackers in India is due to various factors.
The main reason for this is the increase in cyberattacks. As more people use the Internet, the frequency of cyberattacks is also increasing. Various organizations and companies have been targeted by this type of attack. Malicious attackers are always looking for new entry points to exploit system flaws. They use various hacking techniques to gain access to networks and steal sensitive information. Ethical hackers help companies find vulnerabilities in computer systems so that bugs can be fixed before adversaries can exploit them. The second factor is the growing awareness of the importance of maintaining strong cybersecurity measures. At this point, both people and businesses recognize the importance of maintaining good cybersecurity.
They recognize that cyberattacks can expose personal data and affect an organization's day-to-day operations. Ethical hackers help companies protect their networks from various types of cyberattacks. The strict nature of rules and regulations is her third factor. Governments issue many rules and regulations to ensure that businesses comply with cybersecurity standards. Businesses can comply with rules and regulations with the help of ethical hackers. Fourth on the list of reasons is the need to protect a company's reputation. Attacks from cyberspace can damage an organization's reputation. Ethical hackers help protect a company's image by finding and fixing vulnerabilities found in an organization's systems. The sixth reason is because we want to keep costs down. Organizations can suffer financial losses as a direct result of cyberattacks. Ethical hackers help companies reduce operating costs by finding and fixing vulnerabilities in company systems.
Ethical hackers are an invaluable asset to a company's efforts to maintain privacy and security. It helps companies identify vulnerabilities in their systems and implement fixes for those vulnerabilities.
Thursday, November 17, 2022
Mobile Hacking course in Multan to be aware of the attackers 2022
 |
| Mobile Hacking course in Multan to be aware of the attackers 2022 |
Dear viewers, In this blog I am going to tell you about the Mobile Hacking course in Multan to be aware of the attackers 2022 so that your mobile will not be hacked by the hackers. This is the best course offering by our institute with certificate. In this we are going to tell you about the mobile hacking and how hackers can attack our mobile phones. As hacking has become the most demanded field in the world. The cybersecurity companies hire hacking experts so that they can be aware of the attacks of hackers and can protect their sensitive information to leak out. As we know that every company has its own sensitive information by which they are working on their projects so thats why they hire the hacking experts to protect their sensitive information.
In this Hacking course Multan we are offering you different types of courses related to hacking so that no one can trap you. In this I am going to tell you about the Mobile Hacking course in Multan to be aware of the attackers 2022. As we know that today is the era of technology, everyone have their own mobile phones ang they are password protected so that no one can interfere in their privacy. If anyone of you are interested to join our course then you can join it and for more information please contact us.
Now, I am going to tell you that how mobile hacking is done and how we can protect our mobile phones.
Mobile Hacking
Phone hacking includes any way someone gains access to your phone or its communications. This ranges from advanced security breaches to simple wiretapping of unsecured internet connections. It also includes physically stealing a mobile phone or violently hacking it through methods such as brute force.
The problem is that our mobile phones are like little treasure chests. They are filled with a lot of personal information and we use them to do shopping, banking and other personal and financial matters. However, you can protect yourself and your phone by understanding what to look out for and taking a few simple steps. Let's look at some of the more common attacks first.
Types of smartphone hacks and attack shacking software
Software is hacked in a variety of ways, whether hackers gain physical access to your phone to sneak onto your phone, or trick you into installing it via fake apps, sketchy websites, or phishing attacks. can cause problems.
- Keylogging: In the hands of hackers, keylogging acts like a stalker, spying on information as users type, type, and even talk on the phone.
- Trojans: A Trojan is a type of malware that can disguise itself as a mobile phone to extract sensitive data such as credit card account details and personal information.
Here are some possible signs that your phone's software has been hacked.
- A battery that discharges too quickly.
- My phone is running a little slow or getting hot.
- Apps quit abruptly, phones turn off and on again.
- I see unrecognized data, text, or other charges on my bill.
Overall, hacking software can consume system resources, cause conflicts with other apps, and use your data and internet connection to reveal personal information to hackers. All of these can lead to some of the symptoms above.
Phishing attack
These are typical forms of attack. In fact, hackers have also aimed them at our computers for years. Phishing involves hackers impersonating a company or a trusted individual to gain access to accounts and/or personal information. will be These attacks come in many forms such as email, SMS, and instant his messages. What they all have in common are links to bogus websites that try to trick users into handing over this information, or links that install malware to destroy the device or steal information. Learning how to spot a phishing attack is one of his ways to avoid becoming a victim of a phishing attack.
Bluetooth hacking
Professional hackers can use proprietary technology to look for vulnerable mobile devices with open Bluetooth connections. Hackers can carry out these attacks while within phone range, up to 30 feet away, and usually in populated areas. Once a hacker establishes a Bluetooth connection with your phone, they may be able to access your data and information, but this data and information must be downloaded while your phone is within range. As you may have noticed, this is a more sophisticated attack given the effort and skill involved.
SIM card replacement
In August 2019, his SIM card of his CEO of Twitter was hacked by his SIM card replacement scam. SIM card swapping occurs when a hacker contacts the phone company and impersonates you to request that her SIM card be replaced. When the provider sends his new SIM card to the hackers, his old SIM card is deactivated, effectively stealing his phone number. This means that hackers have taken control of your calls, messages, etc. This hacking method involves the seemingly not-so-simple task of impersonating another person, but it clearly happened to the CEO of a large tech company. Protecting your personal information and identity online can help.
5 Ways To Protect Your Phone From Hackers
These simple tips will protect your phone from hackers in minutes.
1. Never leave your phone and data unprotected. Take a few minutes to secure your smartphone today! In addition, it is your first line of defense against hackers. However, if you don't want to use your face or fingerprints, using a numeric passcode is much more effective than using a pattern lock as it's harder to hack. However, make sure the pin you choose is unique and hard to guess. Many people choose a simple his PIN like '1234' because it's easy to remember, but it makes it easier to hack.
2.According to Symantec, 1 in 36 smartphones have high-risk apps installed. Most of these malicious apps are downloaded outside of the Apple App Store or Google Play Store. This is because it bypasses the stringent security measures that Apple and Google employ to protect their smartphones from malware.
Once a high-risk app is installed on your phone, hackers can gain access to personal information such as passwords and credit card details. take it away? —o Only download apps from Google Play or the App Store, and check descriptions and reviews before downloading to see if they look suspicious.
3. Keep your apps and operating system up to date
In addition to downloading apps from Google Play or the App Store, you should also ensure that they are up to date. Hackers can exploit outdated apps, find vulnerabilities in their infrastructure, and gain access to your personal information.
4. For similar reasons, it's also important to keep your operating system up to date. These updates often contain patches for security vulnerabilities found in the operating code, further protecting your phone from hackers. Waiting for your phone to successfully update can be annoying, but it greatly reduces the chances of your phone being hacked. is important to use a VPN. A hacker can connect to any public Wi-Fi router and attempt to access any device using that public network. A VPN hides your connection from cybercriminals and protects you from hacking attacks. However, we recommend that you avoid using public Wi-Fi networks as much as possible.
5. Don't use auto-login
Setting auto-login every time you use the app is convenient, but it is easy to hack. If a hacker has access to your phone and auto-login is enabled, they can easily open any unprotected app and extract all available data from it. It's time consuming, but it's much more secure if you manually enter your password every time you use an app on your phone.
Wednesday, November 16, 2022
Free Ethical Hacking course with certificate for beginners 2022
In this Article I am going to tell you about the Free Ethical Hacking course with certificate for beginners 2022. This is the best course offered by us for all of you and we are providing the certificates for all the students. This course is from basic to advance level for beginners. If anyone of you don't know about the basic of ethical hacking then don't worry about that we will start your course from the basic level to the advance.
If anyone of you are interested in our course then please join our course and for more information you can contact us.
In this course, you will learn what it means to be an ethical hacker and practice the tools and techniques used in ethical hacking.
Hacking has become one of the most common problems facing businesses. However, not all hacks are harmful. In this course, ethical he will learn the basic concepts of hacking. Encryption, vulnerability analysis, and password cracking are also discussed topics. Plus, learn how to compromise servers, infiltrate networks, and obscure your digital footprint. This course is a great place to start your ethical hacking career.
Start Course
This free ethical hacking course introduces you to the basic concepts every aspiring ethical hacker should know. Introducing different types of ethical hackers and ethical hacking tools. Ethical hackers are granted network access and identify system vulnerabilities. This course is a great stepping stone to becoming a trusted cybersecurity expert.
Ethical Hacking:
Hacking is a major cybersecurity problem. Exploits vulnerabilities in computer systems to reveal sensitive information to the wrong person or organization, or to disable group operations. These vulnerabilities are big business, which is why cybersecurity is a critical necessity in the technology age. To keep sensitive information from being accessed, organizations are bridging the gap using security measures such as programs, trained people, and increasingly AI-driven methods. Cybercrime is on the rise, but that doesn't mean businesses aren't responding.
It is a serious problem, but fortunately there are many things that companies can do. It helps protect your operating system by staying one step ahead of loopholes in a number of ways. Ethical hackers attempt to break into systems to reveal potential vulnerabilities. AI can analyze people's movements in the system and quickly identify outliers. Build a career in keeping individuals and organizations safe. We offers ethical hacking courses to develop the necessary skills.
Unlocking Information Security:
Part I. Here you'll learn more about basic information security terminology, vulnerabilities, exploits, and real-life case studies. It also provides an overview of one of the most serious vulnerabilities of all time: buffer overflows. This includes common variants such as variables and stack overflow, simple but effective mitigation techniques such as Canary and his DEP, and many other topics related to ethical hacking and cybersecurity. .
Learn About Hacking Online
Learning things like computer security can help prepare you for the age of technology where identity theft and cyberattacks are becoming more common. EdX.org offers courses and certifications developed in partnership with leading institutions to help you find your way.
Hacking Courses and Certifications
Learn the basics of cybersecurity with this course from the University of Washington, Introduction to Cybersecurity. It provides an overview of common types of attacks, such as denial of service and Trojan horse viruses, and how to deal with them. It also covers the latest news in security systems. If you're ready to go all out, RITx offers a Cybersecurity Micro master. Learn the basics of threat detection, investigative tools, risk management, and network security. It also provides an overview of common hacking tools used by cybercriminals and black hat hackers to exploit vulnerabilities. In addition, stay safe while working on your smartphone, accessing bank accounts, creating strong passwords, using antivirus tools, and understanding everyday activities like phishing. You can take courses designed to help you. We also offers cybersecurity bootcamps.
Fighting Hacking in a Cybersecurity Career
Understanding what hacking is can set you on the path to a long and rewarding career. Whether you become a white hat hacker or work for an organization developing new solutions, you need understanding and expertise. Build a career in helping everyone stay safe and protecting vulnerable people with our Cybersecurity and Hacking course. There will always be people trying to exploit your system, but you can be at the forefront of new security solutions.
Monday, November 14, 2022
Best Ethical Hacking course near me in Multan 2022
 |
| Best Ethical Hacking course near me in Multan 2022 |
In this Article I am going to tell you about the Best Ethical Hacking course near me in Multan 2022 to become the best ethical hacker in future. This is the best course for those who wanted to have Ethical hacking as a profession in the future.
If anyone of you are interested to join our course then you can contact us. The course content of Best Ethical Hacking course near me in Multan 2022 is given below:
- Information security and ethical hacking
- reconnaissance techniques
- system hacking phases and attack techniques
- network and perimeter hacking
- web application hacking
- wireless network hacking
- mobile devices
- Internet of Things (IoT) and operational technology (OT) hacking cloud computing
Hacking involves identifying and exploiting weaknesses in computer systems or computer networks. Cybercrime uses computers and information technology infrastructure to commit crimes. Ethical hacking is about improving the security of computer systems and computer networks. Ethical hacking is legal.
Ethical Hacking:
There are various definitions you can learn about hackers. The term hacker was used in the early 1990s to describe someone with the ability to solve complex problems who could be a good programmer. Now, the definition of a hacker has changed from time to time because it started to have a negative sentiment in the media. I started labeling myself as a person. This image was created by the media to show only the negative side, not the positive side. On the positive side was the person who published the vulnerabilities found in the system, protecting the organization and several users.
Simply put, a hacker can be defined as someone who is creative and able to solve complex problems. For this reason, the term he falls into three different categories.
White Hat Hacker
Hacker known as a security expert. This type of hacker is used by organizations and allowed to attack organizations. Their main task is to find vulnerabilities that attackers can exploit, so they can attack your organization.
Black Hat Hacker
is a type of hacker who uses knowledge for malicious purposes. You are a person who can be called a cracker. The way they use their knowledge is to access user information that could be dangerous to their victims.
Gray Hat Hacker
It is a type of hacker who acts as both a white hat hacker and a black hat hacker . Example:
- A gray hat hacker can act as a security expert for any organization and find vulnerabilities that still exist in the system. However, it can leave a backdoor that can access sensitive information and sell it to the company's competitors.
What types of hacking are there?
There are several ways to hack a system -
1. Computer Hacking or System Hacking - This type of hacking involves breaking into individual systems or computers within a network. Includes access. This is common when the target is a single target or when the goal is to steal information from a network of computers. Breaking into systems and identifying vulnerabilities is the job of an ethical hacker.
2. Network Hacking or Wireless Network Hacking - Wireless hacking is the process of stealing, capturing, or monitoring wireless packets within a particular network. Once hackers gain access to your wireless network, they can also access your passwords, chat sessions, user history, and more. Ethical hackers use similar methods to infiltrate wireless networks and find new alternatives used by black hat hackers.
3. Email Hacking - In the digital world of business, emails contain highly sensitive data and information that hackers may be interested in. Email hacking involves hacking a network to obtain email passwords or gaining unauthorized access to an individual's or company's employee's email. This can reveal someone's private life or leak sensitive data from business emails. Phishing attacks (pervasive) can also allow users to compromise their personal information and data security.
4. Hacking a website or hacking a web application – Unethical hackers may be interested in hacking a website or web server because it can negatively impact your business. This can lead to prolonged website downtime (loss of business, detection and recognition), software and database theft, and even permanent damage. However, ethical hackers attempt this with permission and suggest ways to fix cracks.
5. Hacking passwords can be part of hacking a computer or system: Hackers use data stored on computers and servers to gain access to passwords for websites, computers, emails, accounts, etc. and use this information for malicious purposes. Ethical hackers do this using similar methods, identifying all security measures that can be taken to prevent this.
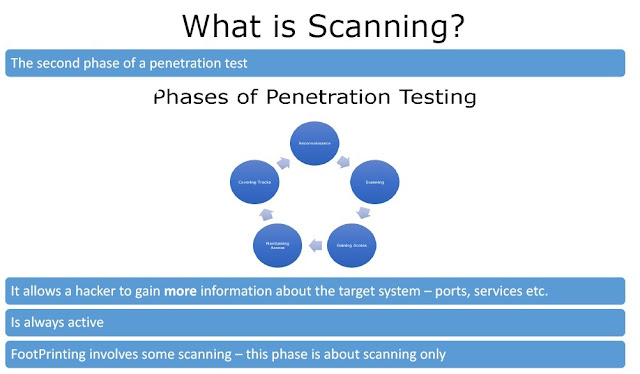
Phases of Ethical Hacking:
Ethical hacking has five phases to ensure all cybersecurity infrastructure is covered while ethical hackers test an organization's network. These phases will help you understand the basics of ethical hacking.
Reconnaissance - This is the first stage of ethical hacking, often called the preparatory stage. At this stage, ethical hackers gather enough information, plan, and prepare to attack. The first phase of reconnaissance is garbage collection, where ethical hackers try to find useful information such as old passwords, employee databases, customer databases, and archived financial information. The next step is the footprint. Hackers collect necessary information related to the hacking process, such as: Examples: security frameworks, IP addresses, etc.
Scanning - Scanning is the process of quickly accessing the outer layers of a network or system's security framework. At this stage, hackers are also looking for relevant information. The first step is pre-attack scanning, which uses intelligence from reconnaissance to gather more information. The second step is sniffing or port scanning. Hackers use tools such as vulnerability scanners, port scanners, and dialers to monitor networks. Finally, information extraction gathers information about ports, physical machines, and system details to prepare for hacking attacks.
Gaining Access – After collecting all relevant information, the next step for hackers is to gain access to a network or system. When this happens, hackers gain full control with access to network details and individual systems. or to allow enough time to achieve the hacking objective. Additional attacks are also launched if the hackers need more time or want to inflict more damage.
Hide Your Footprints – Evading guards and built-in security systems is just as important as gaining access. This is done by following procedures such as closing open ports, clearing log files, clearing all cookies, etc. This prevents hacking attempts from being traced back to the hacker.
Thursday, November 10, 2022
Free Cybersecurity course in Multan to be aware of hackers attack 2022
 |
| Free Cybersecurity course in Multan to be aware of hackers attack |
Dear viewers, In this blog I am going to offer you Free Cybersecurity course in Multan to be aware of hackers attack so that you will be able to be aware of the hackers attack. This is the best course for those who wanted to be successful in the field of hacking and protect their systems away from the hackers attack.
This is the best course offering to you, If anyone of you are interested to join our course then you can contact us.
Now I am going to explain you about the Free Cybersecurity course in Multan to be aware of hackers attack.
What is Cybersecurity?
Cybersecurity is the protection of systems such as hardware, software, and data connected to the Internet from cyberthreats. This practice is used by individuals and businesses to protect against unauthorized access to data centers and other computerized systems.
Types of Cybersecurity:
The three main types of cybersecurity are:
- network security
- cloud security
- physical security.
Your operating system and network architecture make up your network security. It can include network protocols, firewalls, wireless access points, hosts, and servers.
Network security:
Network security includes access control, viruses and antivirus software, application security, network analysis, network-related security types (endpoint, web, wireless), firewalls, VPN encryption, and more.
Cloud security:
Cloud security, additionally called cloud computing security, is a set of safety features designed to defend cloud-primarily based totally infrastructure, applications, and records. These measures make certain consumer and tool authentication, records and aid get entry to control, and records private protection.
The 3 major forms of cloud deployment fashions are private, public, or hybrid.
Physical security:
Physical security is the protection of personnel, hardware, software, networks, and data from physical actions or events that could cause significant loss or damage to a business, government agency, or agency. This includes protection against fire, flood, natural disasters, robbery, theft, vandalism and terrorism.
Sensors, alarms, and automatic notifications are examples of physical security detections. 3. Delay - There are certain security systems designed to delay intruders attempting to enter a facility or building. Access controls such as, for example, requesting a card key or mobile ID card is one method of delay.
What Is a Cybersecurity Professional?
As data breaches, hacks, and cybercrime reach new heights, organizations turn to cybersecurity professionals to identify potential threats and protect valuable data. increasingly dependent. It makes sense that the cybersecurity market is expected to grow from $152 billion in 2018 to $248 billion in 2023.
So what do cybersecurity professionals do?
What they can do on a daily basis:
- Find, test, and fix vulnerabilities in your organization's infrastructure.
- Monitor systems for malicious content
- Identify network breaches
- Install regular software updates, firewalls, and antivirus protection
- Strengthen areas where attacks may have occurred
They work in one or more of these common Cyber Security domains to keep data safe:
Asset security:
Analyze networks, computers, routers, and wireless access points
Security architecture and engineering:
Standardize security policies and procedures
Communication and network security:
Regulate cloud storage and data transfer
Identity and access management:
Track user authentication and accountability
Security operations:
Monitor security to identify attacks
Security assessment and testing:
Test security policies to ensure compliance with industry standards
Software development security:
Create and repeatedly test code
Security and risk management:
Identify potential risks and implement appropriate security controls
Cyber Security experts employ different tactics to secure computer systems and networks.
Some of the best practices include:
- Using two-way authentication
- Securing passwords
- Installing regular updates
- Running antivirus software
- Using firewalls to disable unwanted services
- Avoiding phishing scams
- Employing cryptography, or encryption
- Securing domain name servers, or DNS
Importance of Cybersecurity:
In today's connected world, everyone benefits from an advanced cyber defense program. On a personal level, cybersecurity attacks can have consequences ranging from identity theft to extortion attempts to loss of important data such as family photos. It relies on critical infrastructure such as Protecting these and other organizations is essential for our society to function.
Everyone also benefits from the work of cyber threat researchers, such as Talos' team of 250 threat researchers studying new threats and cyber attack strategies. They discover new vulnerabilities, educate the public on the importance of cybersecurity, and enhance open source tools. Your work makes the internet safer for everyone.
What are the top security threats?
First, we need to understand the difference between information security and cybersecurity, and the types of threats we face almost every day. Both the information security threats that exist today and the emerging threats that will surely plague organizations tomorrow.
Malware
The most common cyber attack is malicious software, better known as malware. Malware includes spyware, ransomware, backdoors, Trojan horses, viruses, and worms.
spyware is software that allows an attacker to obtain information about a user's computer her activities by covertly transferring data from the user's hard drive.
ransomware is designed to encrypt files on your device and render all files (and the system based on them) unusable. Malicious attackers usually demand a ransom in exchange for decryption. The
backdoor bypasses normal authentication procedures to gain access to systems. This allows attackers to remotely access resources within your application, Databases and file servers. It also allows malicious actors to issue system commands and update malware remotely.
Trojan is malware or code that acts as a legitimate application or file to trick users into loading and running malware on their device. The purpose of a Trojan horse is to destroy or steal an organization's data or damage a network.
A computer virus is malicious computer code designed to spread from device to device. These self-cloning threats are usually aimed at damaging your computer or stealing your data. The
worm is malware that spreads copies of itself from computer to computer without human intervention and does not need software attached to his program to cause damage.
Malware is usually installed on a system when a user opens a malicious link or email. Once installed, the malware can block access to critical components of your network, damage your system and export sensitive information to unknown destinations.
- Prevent malware-based cyber-attacks with proven antivirus and antimalware solutions, email spam filters, and endpoint security solutions.
- Make sure you have all the latest cybersecurity updates and patches.
- Require employees to complete regular cybersecurity awareness training sessions to teach employees how to avoid suspicious websites and not engage in suspicious emails.
- Restrict user access and application privileges.
Phishing and Spear Phishing
phishing is a form of social engineering that attempts to trick users into revealing sensitive information such as usernames and passwords, bank account information, social security numbers, credit card details, and more.
Hackers typically send phishing emails that appear to come from trusted senders such as PayPal, eBay, financial institutions, or friends and colleagues. Fake messages try to trick users into clicking links in emails. This redirects users to fake girlfriend websites that ask for personal information or install malware on the device.
Opening attachments sent in phishing emails can also install malware or allow hackers to remotely control your device.
Spear phishing is a more sophisticated phishing attack in which cyber criminals target only privileged users such as system administrators and executives. Attackers can use someone's social media account details to appear more legitimate to their targets.
Other types of phishing include smishing, vishing, clone phishing, domain spoofing, URL phishing, watering hole phishing, and evil twin phishing. Everything can get very expensive.
Organizations can take several steps to reduce the likelihood of phishing.
- Emphasizes the importance of phishing reports.
- Run a random phishing simulation.
- Website pushes HTTPS for a secure and encrypted connection.
- Institutional Access Control Policies and Procedures.
- Use reliable email and spam filters.
- Two-factor authentication required.
- Use email encryption and email signing certificates.
Man-in-the-Middle (MITM) Attacks
These attacks occur when a malicious actor gets in the middle of her two-way communication. Once an attacker intercepts incoming messages, they can hack your system.
Distributed Denial of Service (DDoS)
DDoS attacks aim to bring down a company's website by flooding the server with requests. It's like constantly calling your company phone number. Therefore, legitimate callers only get a busy signal and never get connected.
This attack sends requests from hundreds or thousands of IP addresses. These IP addresses may also have been compromised and tricked into continuously requesting your company's website.
A DDoS attack can overload a server, slow it down significantly, or take it temporarily offline. These shutdowns will prevent customers from visiting her website to complete orders.
Structured Query Language (SQL) Injection
A SQL injection attack occurs when a cybercriminal uploads a malicious SQL script to try to access a database. If successful, malicious actors can view, modify, or delete data stored in the SQL database.
Domain Name System (DNS) Attacks
DNS attacks are cyberattacks in which cybercriminals exploit vulnerabilities in DNS. Attackers exploit her DNS vulnerabilities to redirect website visitors to malicious sites (DNS hijacking) and exfiltrate data from compromised systems (DNS tunneling).
Wednesday, November 9, 2022
Best Ethical Hacking Institute in Multan to become the Professional Ethical hacker in future 2022
 |
| Best Ethical Hacking Institute in Multan to become the Professional Ethical hacker in future |
Dear Viewers, In this Article I am going to tell you about the Best Ethical Hacking Institute in Multan to become the best Ethical hacker in future. Alhuda Institute is the best for doing Ethical hacking course. This course is for those who wanted to become the best in the Ethical hacker in the Future.
If anyone from you wanted to become the Professional Ethical hacker in the future can join our best institute for Ethical hacking in Multan.
If anyone of you are interested to join our Best Ethical Hacking Institute in Multan to become the Professional Ethical hacker in future can join our course and for more information you can contact us.
Now I am going to explain about the Best Ethical Hacking Institute in Multan to become the Professional Ethical hacker in future.
Alhuda Institute is the best for learning Ethical hacking and to become Professional in future or you can have Ethical hacking as a profession in the future. There are many opportunities in the future of Ethical hacking.
Ethical hacking is a lucrative career choice for many, and not without reason! In this Ethical Hacking Career article, we'll take a look at the various factors that guide you on your path to becoming an ethical hacker.
- Who is an Ethical Hacker?
- Requirements to Become an Ethical Hacker
- Ethical Hacker Roles and Responsibilities
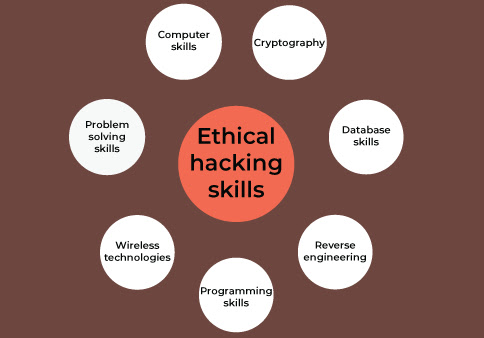
- Ethical Hacker Skill Set
- Ethical Hacker Job Trends
- Ethical Hacker
- Ethical Hacker Job Profiles
- Companies Hire Ethical Hackers
Who is an Ethical Hacker?
“To beat a hacker, you have to think like one” – Ethical Hacking Council
Hacking is the process of finding vulnerabilities in a system and using these found vulnerabilities to gain unauthorized access into the system to perform malicious activities ranging from deleting system files to stealing sensitive information. Hacking is illegal and can lead to extreme consequences if you are caught in the act. People have been sentenced to years of imprisonment because of hacking.
Nonetheless, hacking can be legal if done with permission. Computer experts are often hired by companies to hack into their system to find vulnerabilities and weak endpoints so that they can be fixed. This is done as a precautionary measure against legitimate hackers who have malicious intent. Such people, who hack into a system with permission, without any malicious intent, are known as ethical hackers and the process is known as an ethical hacking.
Requirement to Become an Ethical Hacker
How your ethical hacking career begins depends on your current field of work. If you’re not in an IT field you should definitely try shifting into one. Even though most jobs require you to have a Bachelor’s degree in computer science or cybersecurity-related field, exceptions are made for people with sound knowledge of operating systems, databases and networking! Also, it is nigh impossible to directly become an ethical hacker. Most ethical hackers begin their career as tech support engineers who climb their way up, by earning certifications like CCNA and CISSP before working towards the ultimate CEH certification. After earning your CEH certifications, is the time to market yourself as an ethical hacker!
Cyber Security Course
Now let us go over the roles and responsibilities of an ethical hacker.
Roles & Responsibilities of an Ethical Hacker
There seems to be a general misconception that a person with an ethical hacking career is only responsible for penetration testing of systems and applications. This is not true, and an ethical hacker is responsible for much more.
Scanning open and closed ports using Reconnaissance tools like Nessus and NMAP
Engaging in social engineering methodologies
Examining patch releases by performing vigorous vulnerability analysis on them
An ethical hacker will see if he/she can evade IDS (Intrusion Detection systems), IPS (Intrusion Prevention systems), honeypots and firewalls
Ethical hackers can employ other strategies like sniffing networks, bypassing and cracking wireless encryption, and hijacking web servers and web applications
An ethical hacker strives to replicate the working of a black hat hacker by analyzing the defense protocols and social-engineering aspects of an organization. His job is to make sure the organization reacts to these situations well enough if they are already not doing so. Go through our Ethical Hacking Course to explore more about ethical hacking. This course will teach you the most current hacking techniques, tools and methods that hackers use.
Ethical Hacker Skill Set
A person with an ethical hacking career is expected to be proficient in database handling, networking, and operating systems and also have excellent soft skills as they need to communicate problems regarding security to the rest of the organization. Other than these generalized skillsets, an ethical hacker also have a good grasp on the following skills:
- Network traffic sniffing
- Orchestrate various network attacks
- Exploit buffer overflow vulnerabilities
- SQL injection
- Password guessing and cracking
- Session hijacking and spoofing
- DNS spoofing
Apart from this, an ethical hacker must be a creative thinker because black hat hackers are constantly coming up with ingenious ways to exploit a system and it is an ethical hacker’s job to predict and prevent such breaches.
How Much you Earn from Hacking?
According to Pay scale, the average annual salary for a certified ethical hacker is $80,074. According to Stephen Graham, senior director of the EC Council, the average starting salary for a certified ethical hacker is $95,000. No Wires Security founder Eric Geier estimates conservatively $50,000 to $100,000 a year for the first few years of a job, depending on employer, experience, and education. Those with a few years of experience, especially those working as independent consultants, can earn over $120,000 a year. (Computing/Network/Information Technology)
Information Security Manager
Penetration Tester
Companies That Employ Ethical Hackers
Ethical Hackers Can Help Your Website Or Anything You Need You can find a job in any company with do it on the web. This includes higher education institutions such as MIT, and private companies ranging from logistics services to data warehousing companies. Apart from that, there are also opportunities to work for military and top secret agencies such as CIA, Mossad, NSA
Now I am going to end the blog Best Ethical Hacking Institute in Multan to become the Professional Ethical hacker in future. If anyone of you are interested then join our course and for more information please contact us.